Bitwarden - Open Source Alternative to LastPass and 1Password
In this article, we are looking at Bitwarden as a password manager for individual or professional use. Reviewing what is done in terms of encryption for your passwords and talking about self-hosting!

What are you talking about?
Passwords, passphrases, keys and other static secrets still form the cornerstone of information security. So hard to remember that we often forget about them and end up using the same variations or worse, a single password for everything. Such a weak proof of your identity and yet often enough to impersonate your account on social networks, read your emails and send malicious links to all your contacts.
What is the solution ? Some say write them down and store them in a locked drawer. However while you are abroad enjoying your holidays and urgently need to access an online service, your passwords will be impossible to fetch. In case of fire in your house, flood or other disasters your passwords will be lost forever. There is a much better approach which is more secure and more practical. This is called a password manager.
Password manager ?
A password manager is a piece of software that lets you manage your passwords. It will typically allow you to store all your passwords into an encrypted vault which is accessible via a master password. Yet another password? Yes but this a unique (very strong) password or passphrase to protect hundreds or thousands of your "regular" passwords that you use within websites and applications. This is very important to only use this master password to secure your vault and not for anything else. The underlying security of the password manager relies on your ability to keep this master password secret.
A password manager will also offer you side services that are very useful such as generating random passwords of a given length and complexity. In fact, for every registration form you will complete, you don't need to think about creating a password you just generate a new one and store it within your password manager. A good password manager will also provide you with browser add-ons and mobile applications to fill-in automatically login fields so that you don't need to type these very long and complex (hence more secure) passwords.
I have written a first article more than 2 years ago about leveraging an existing Nextcloud installation to host a password manager extension. Since then, the landscape has changed and although it might remain a viable option, I would like to talk today about a better alternative called Bitwarden.
Although the leaders of the market: LastPass or 1Password are well-known and are very good alternatives (with a preference for 1Password). I wanted to talk more about Bitwarden because of two major advantages :
- It is open source. It means that if you are tech savvy like me you can review the source code and see for yourself what is under the hood, including the encryption algorithms storage and handling of key material.
- It has great support for self-hosting. Being a client-server model, you can host the vault on your own server. If like me, you like to deploy software on your own dedicated server instead of relying on cloud services hosted outside of your control, then Bitwarden is ideal as a password manager. They provide ready to deploy docker images so that your full setup can be up in a few minutes. I will talk in a subsequent article about my own Docker-Compose setup including the Bitwarden containers.
Here is an example of the interface on MacOS but the look&feel of all clients is similar.
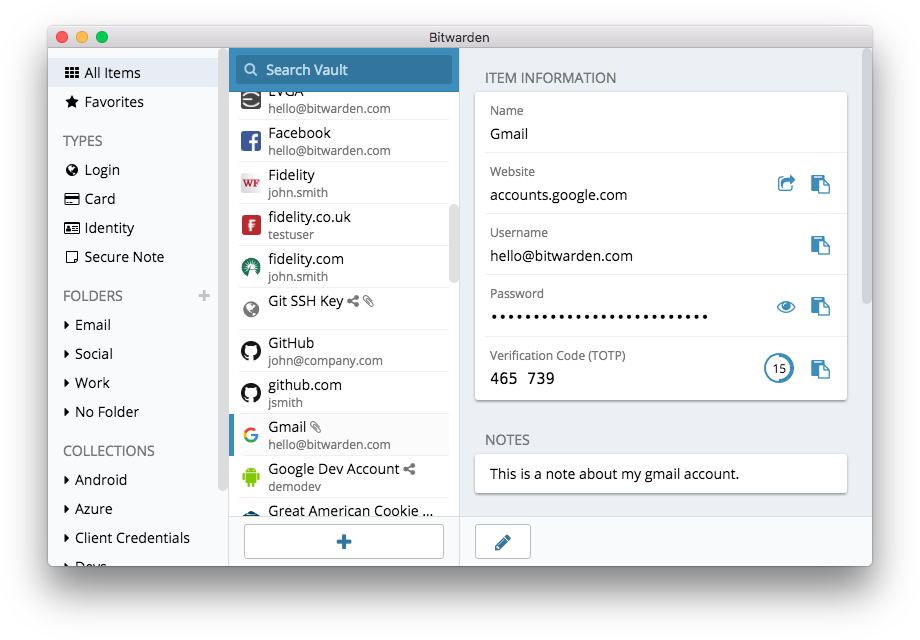
Bitwarden
Behind this strange name, what is it and how does it work? What are the strength and weaknesses of this password manager? Keep reading this section for an in-depth analysis.

How are your passwords secured?
Unsurprisingly it relies on encryption technologies and in this case the AES algorithm with a 256 bit long key which is the most secure version and is even approved by governments for the storage of secret information. AES relies on a secret key to encrypt and decrypt data, in this case and you have probably guessed it, the secret key will be your master password mentioned earlier.
Now you may wonder how can they use a 256 bit key from a variable length password you have chosen as master password (e.g. using 20 printable characters)? They use again a well known algorithm called PBKDF2 or Password Based Key Derivation Function 2 which will repeat an operation (in this case SHA-256) many times to make it relatively slow to get the derived key. The goal here is to make bruteforce attacks which rely on trying millions of possibilities per second inefficient[1]. The SHA-256 algorithm will always output a value of a fixed-length (256 bit) and at the end of all the iterations (the number can be customized in Bitwarden) we obtain the derived key that will be used as the private symmetric key with AES-256 to encrypt each one of your passwords. Although I haven't seen it clearly mentioned in the documentation, line 143 in this JS source tells us that the CBC mode is used.
Each password will also get a unique and random IV (initialization vector) stored next to the encrypted password in the database. This IV will allow for 2 separate accounts that use the same password to get very different ciphertext in the database. An HMAC is also computed to verify the integrity of the stored password. This encrypted database is stored in a data.json file, here is an example of what is in there:
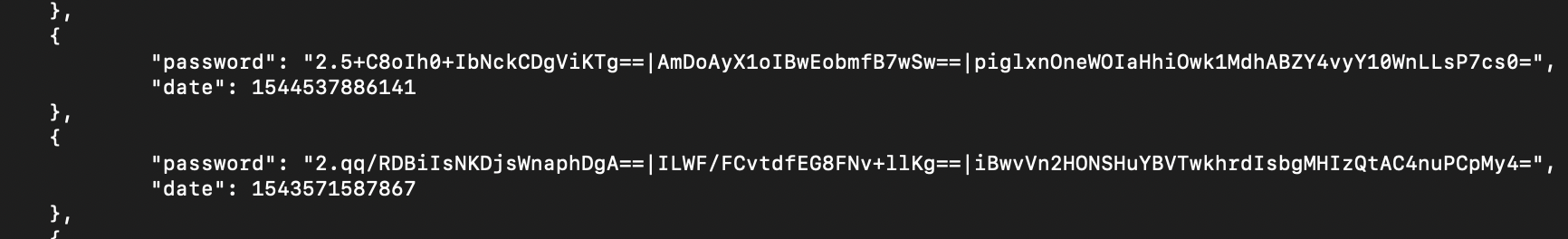
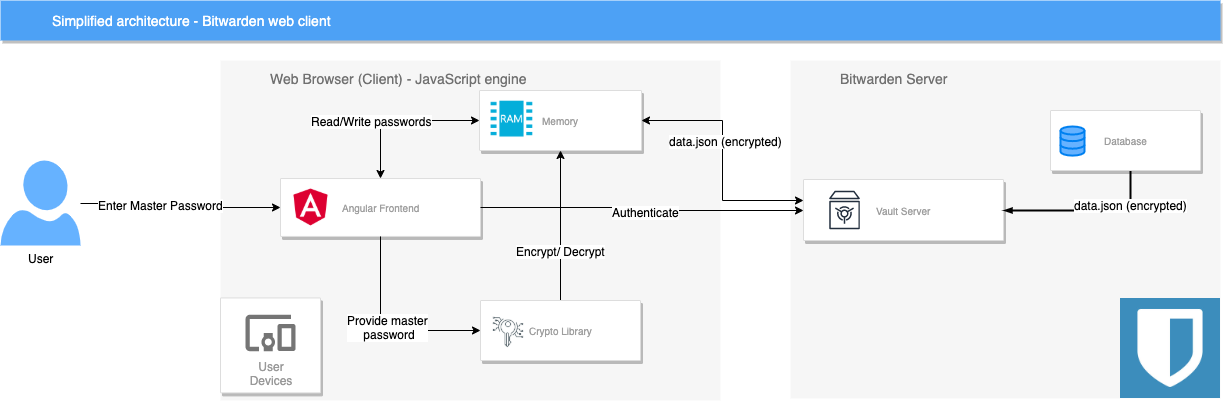
It is important to note that this encryption process will always happen on the client side (e.g. within your browser if you use the website or the add-on), only transmitting already encrypted data to the server. So if attackers could get a copy of the server disk, they would not be able to access your passwords in clear. To perform the encryption operations themselves, Bitwarden uses well-known libraries either in Javascript (for desktop and web clients) or in native languages for mobile applications. You can consult their knowledge base to learn more about it. Here is a very simplified view of the interactions between the client and the server which shows that all the encryption and decryption operations are performed client side, the server only received the encrypted data which are stored in the database. Of course, the communication between client and server is secured at the transport layer via TLS.
They also take security seriously by conducting independent security audit and fixing all vulnerabilities found in a short timeframe.
Hosted or managed?
As mentioned in the previous section, if your server is comprised, the database is encrypted and thus your passwords cannot be recovered. However a smart attacker could try to alter the JS code to steal the master password when you enter it in your browser. That is more advanced but not totally impossible. So maintaining a secure environment is still important.
In any case Bitwarden offers you two options for the server. The first one is to use their own infrastructure which leverages Microsoft Azure so you can have confidence on their availability. This would be the preferred option for most of the people because the service is entirely managed by Bitwarden and it's free ! There is of course a premium plan to support the developers and get you some extra features like 2FA with Yubikey and password sharing but most people should be fine with the free tier.
The second option is to host the Bitwarden vault on your own server and this may appeal to you if, like me, you like hosting your own services and you perhaps already have one or two servers that you can use for that purpose. I would not recommend this for people who do not have any infrastructure yet as the cost (both in money and time) to maintain your dedicated infrastructure just for Bitwarden will not be worth it. If you consider this option you should look at the documentation here, which basically describes how to install docker and deploy all the containers required for Bitwarden. One important note: don't forget to backup! If the storage in your server fails completely you can loose access to your passwords, even though a local cache can be recovered from your synchronized devices (laptops, phones...). As everything is already encrypted in the database you don't need to encrypt your backup.
The hosted alternative can also be used by companies which in this case will be required to license their installation but will receive support while being in charge of the infrastructure. This could give additional trust and allow for compliancy with existing baselines for servers, databases etc. An existing MSSQL server could for instance be leveraged. This would offer a significant advantage over isolated fat clients such as Keepass which could incur loss of passwords in case of devices failures or employees taking important passwords with them when they leave the organization.
Two step verification
To access the web vault, there is a possibility to enable a second factor. Note that this will only be used for authentication, not for the actual encryption of your passwords which is entirely based on your master password. However, this could still be useful to prevent attackers from accessing your vault via the web if they have successfully stolen your master password (via key logging for instance). Nevertheless, if they also manage to steal your encrypted vault, either via server compromise or the cache stored on your end devices, then the game is over.
Conclusion
In this article, I have performed a review of the Bitwarden password manager based on personal experience, documentation and research. If you have never used a password manager before, you should give the free account for personal use a try and use browser extensions and fat clients on your different devices. If you are looking for an open source and reliable product that you can install on your own server, you can get started in a few minutes with the docker containers.
I hope this overview was not too technical for you, let me know about your favorite password manager!
1. While preparing this article I realized that some people where criticizing the use of SHA-256 within PBKDF2 due to the fact that SHA-256 can be well optimized on some ASICs hardware (used for instance to mine Bitcoin) and thus the key derivation function is not slow enough to prevent efficient bruteforcing. There is a proposition in the Bitwarden forum to move to another algorithm for the key derivation, you can see it here. In the meantime you can adjust the iterations count to the maximum possible if you feel this is an important risk in your use case.